Cyber Security
EFFECTIVE Permissions
NEVER TAKE IT FOR GRANTED!
Here is one of the primary root causes of data breaches.
It’s one thing to identify who did something after it happened - auditing, it's totally another to know why it was allowed to happen in the first place!
Remember: Auditing tools alone let you react, but not prevent.
Data Rover™ has more than just an Auditing Tool. Auditing tells you what was done and when… That’s toooo late.
Misconfiguration, or just pure human error, is the root cause as to why the keys to the kingdom were left lying around.
Checking these privileges is extremely laborious, resource intensive and time consuming. So much so that many companies give up and close their eyes hoping nothing happens. But it ALWAYS HAPPENS.

You need Data Rover before to prevent such occurrence ever happening.
EFFECTIVE PERMISSIONS. What are they?
"Effective permissions" are the real privileges that users have on a file or folder.
Giving users the right, and ability, to Copy, Modify, Delete, or Move or even allow or disallow access!
Here is where Data Rover excels in giving you a complete view of the real access privileges to the files and folders on all your storage devices.
"Effective permissions" are the real privileges that users have on a file or folder.
Giving users the right, and ability, to Copy, Modify, Delete, or Move or even allow or disallow access!
Here is where Data Rover excels in giving you a complete view of the real access privileges to the files and folders on all your storage devices.
Use Data Rover and make your company a better place.
Data Analytics
Check any security flaws and eliminate issues.
Simplify the management of permissions and the protection of data.
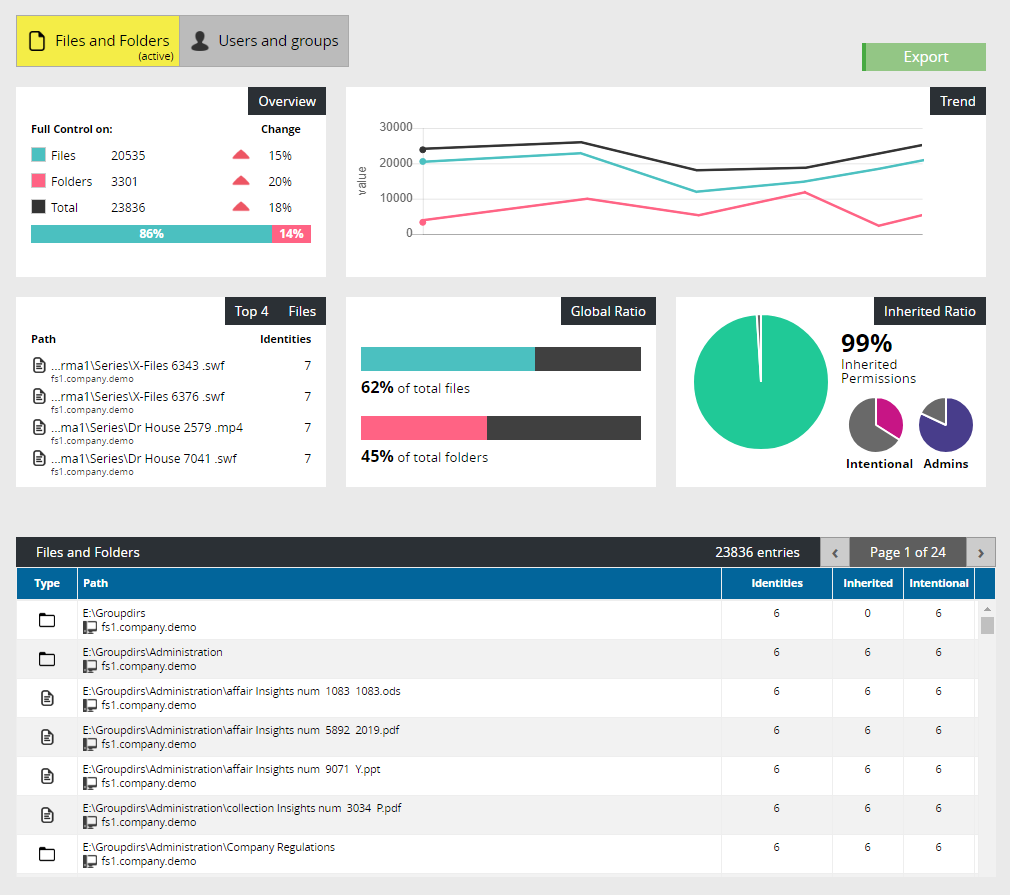
Data Analytics gives one a complete and detailed on-demand view of the access privileges to the files and folders present across the entire company's storage devices.
Use the Point-In-Time feature to check a past configuration allowing you to evaluate the differences.
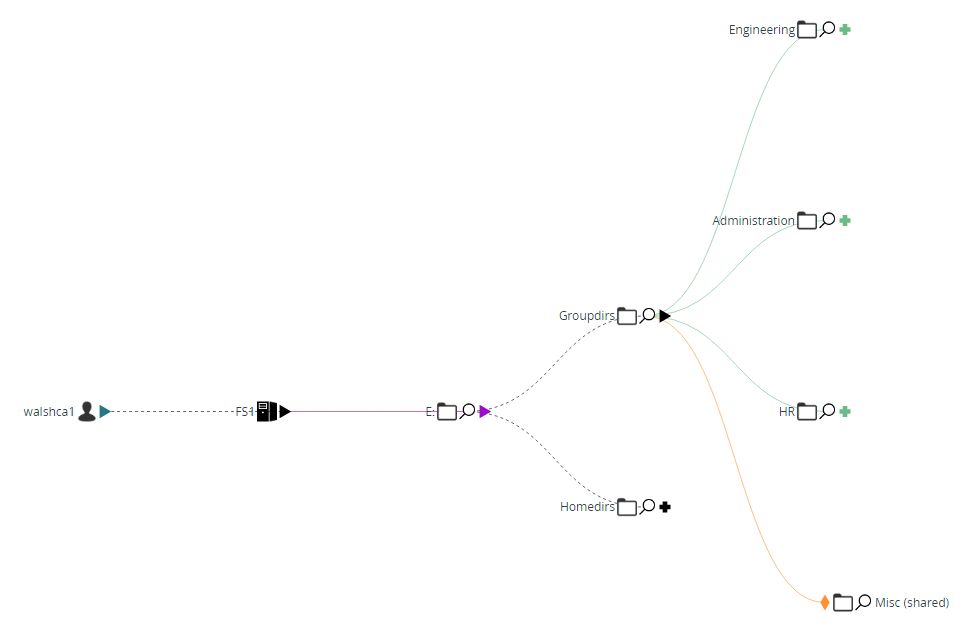
In addition to the common table-view you can navigate within the files and folders using our dynamic “Security Tree” diagram.
The permissions are graphically represented and are easily recognisable thanks to a recurring colour scheme.
Data Rover's Time machine!
Toggle back and forth in time and check, or reset, identity privileges
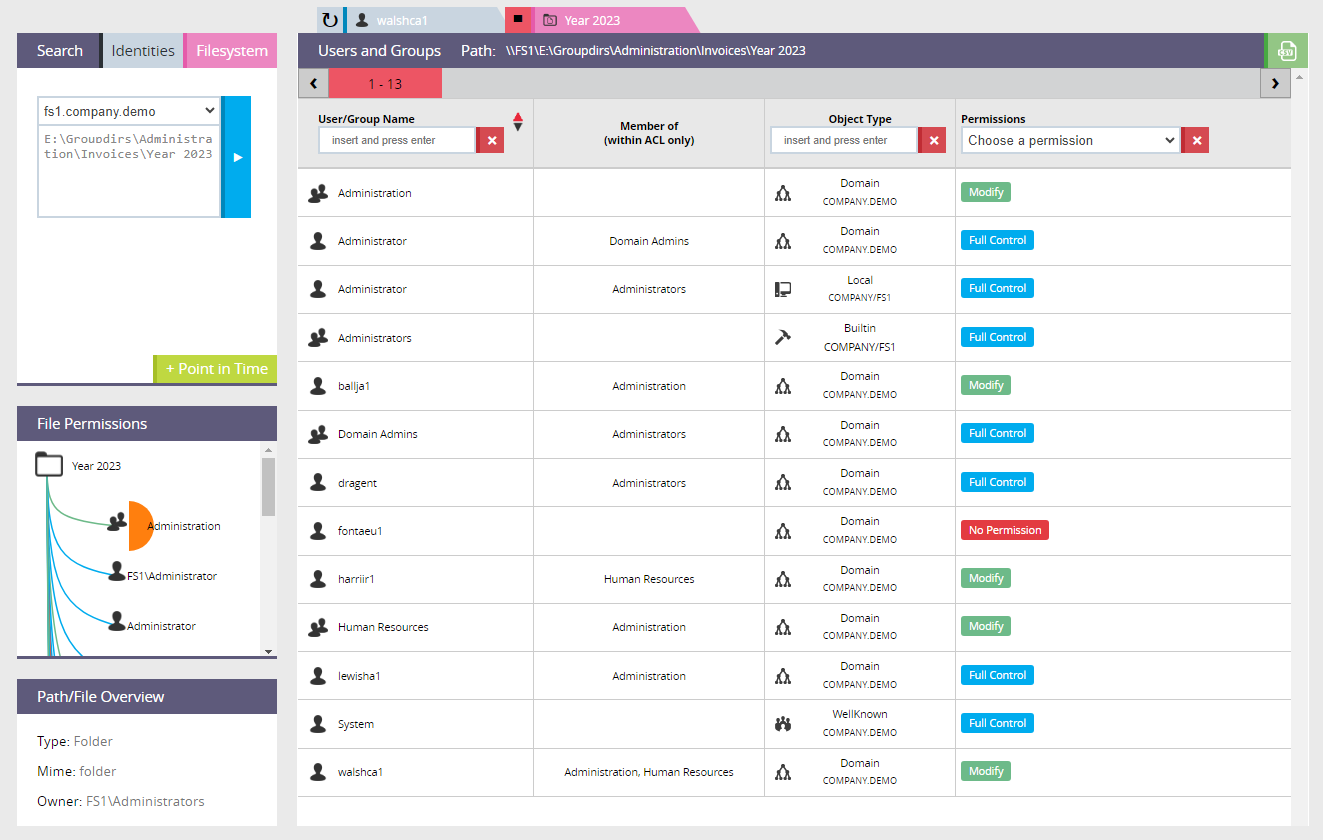
Select a user or group and precisely see which files and folders they have access to and with what level of privilege.
Select a specific file or folder and display the complete list of all users and groups who have the possibility of working on the specified resource.
Determine who can e.g., access, modify or delete specific information and so be able to identify eventual security holes or unauthorised access issues.
Security Reports
Concentrate on specific risk areas and deliver detailed analysis on the privileges that can be potentially incorrect or dangerous.
Example Reports:
Full Control
Delete
Take Ownership
Change Permissions
Your file system contains critical business data and sensitive information that is the fruit of thousands of hours of work.
A data theft, loss and corruption if left unprotected leads to downtime and service disruption.
Downtime and reputational damage is extremely costly.